Those of us who work on the development of Bitcoin every day agree on one thing: we want to scale Bitcoin in a trustless way, but we want to do it in a way that preserves, if not improves, the privacy aspects of Bitcoin. Lightning Network may be one solution.
What is Lightning Network?
Lightning Network is the only solution to Bitcoin scalability that works in a completely trustless manner. This is definitely its most important property as it connects directly to Bitcoin’s decentralized and peer-to-peer roots.
Lightning Network is thus a second layer that lives and exists on top of Bitcoin, which theoretically delivers extremely valuable and necessary properties: scalability, security and privacy.
Types of transactions on Bitcoin
Lightning Network is, as mentioned earlier, a second layer of Bitcoin. For this reason, whenever we talk about LN privacy, we have to think about these different layers simultaneously; doing the opposite would not make sense since, without the base layer of Bitcoin, LN would not exist.
For the same reason, someone who wants to spy on us will surely be present and operate on both levels. Examples of these might be your favourite government agencies such as the CIA and NSA, or private companies that make a business out of surveillance of Bitcoin (and its users) such as Chainalysis and Elliptic, or an individual who wants to track our funds and has enough technical knowledge and tools to do so.
Opening a channel
To function, Lightning Network essentially requires the creation and transmission of two on-chain transactions. First, it requires the opening of a payment channel with another node. This opening transaction takes place on the blockchain and therefore still has a perennial, immutable and transparent digital fingerprint.
Once this transaction is confirmed and the payment channel opened, the two counterparts of this channel can send transactions to each other indefinitely without creating and writing further transactions on the main Bitcoin blockchain. If this channel is then used over time to such an extent that its liquidity is depleted, or if the relationship between the two counterparties is simply terminated, the channel is closed.
Closing a channel
The transaction to close the channel is also written and transmitted to the main Bitcoin network, which, as I repeat, maintains a perennial, immutable and transparent fingerprint.
On Lightning Network users can make as many transactions as they want, but in any case, two of them will always be visible and analyzable perpetually on the main Bitcoin network.
An important point to remember: whenever we talk about privacy, we should not forget that a potential threat is present and operates on both layers.
On the main layer (Bitcoin’s blockchain), the adversary will surely make a careful analysis of the transaction graph to assess and see where the channel was opened and closed, and how it was closed.
Whereas on the second layer of Bitcoin (Lightning Network) the adversary will surely be listening and recording all the information that is exchanged between the various nodes to allow the Lightning Network to function (gossip p2p) through the different public channels present. This is possible because of the concept of a trustless network: a network without authorization in which everyone can participate and in which everyone can create new nodes and new channels.
This is the main reason why the argument that “Lightning Network is anonymous, allows anonymous transactions and improves privacy to perfection” is extremely wrong and harmful. It is not true to say that since we don’t write off-chain transactions on the blockchain then we can be safe. There are still transactions that are exchanged and communicated between various entities, most of the time unknown.
Potential attackers we should defend against
In the case of on-chain analysis, an adversary is usually considered as having access to the blockchain. This is a fairly unfavourable point, given that the public and transparent nature of Bitcoin allows anyone to see every transaction and address balance.
In a more advanced case, we also assume that the adversary can hear and feel what is happening at the network level. For example, we can imagine someone being able to link our IP address to the transaction we have just transmitted on the Bitcoin network. If this transaction results in the opening of an LN channel, then this adversary will be able to link our IP to the identity of our LN node as well.
This is referred to in jargon as the “on-chain adversarial model” and assumes that such an adversary can listen to everything that happens at the network level and simultaneously see what is being exchanged and written at the level of the blockchain.
In the case of Lightning Network, we also assume that the adversary is present within the network. Typically, on LN, an adversary who wants to deanonymize us has many open payment channels with many other nodes in the network and is well integrated into the Lightning Network graph, i.e. has good network reach.
Most likely, whenever you send a payment on LN, there will be several intermediaries between you and your counterpart, unless you have a direct channel with them. We can therefore assume that some of these intermediaries are actually controlled (directly or indirectly) by your potential adversary. If this were the case, the opponent could record all information about your payments.
This is the way most adversaries operate today. In Lightning Network, when thinking of a perfect adversary, then we assume that the adversary has many open payment channels with other nodes, a lot of liquidity and capacity in terms of satoshi value and records all public information.
For this reason, it is important to avoid opening channels with the largest nodes within the network, even if they are “trusted” nodes, i.e. controlled by entities we trust (think for example of well-known companies in the Bitcoin ecosystem that also have nodes on Lightning Network).
Anonymity and privacy in Lightning Network
The concept of privacy and anonymity set on LN is determined by our “neighbours”. Sometimes, it is preferable to choose smaller nodes rather than large centralized hubs. This is most often to the detriment of the fees we would have to pay to such nodes and the speed of our transactions, but it will help us enormously in the privacy aspect.
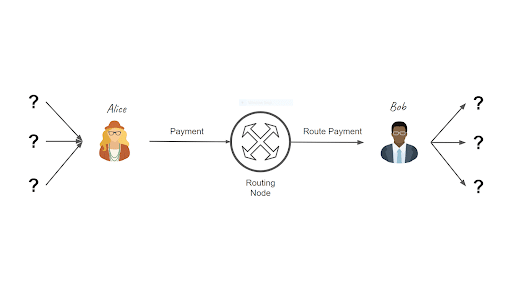
Image credits: Mastering the Lightning Network by Andreas M. Antonopoulos, Olaoluwa Osuntokun, Rene Pickhardt
The more paths and channels there are on the Lightning Network, the more the privacy of users is preserved.
This is actually only one of the many possible attacks that happen every day on LN. Among others, we can mention the disclosure of channel balances, Denial of Service, Commitment jamming, de-anonymization of nodes and funds, Topology-based attacks, and much more…
The objectives of Lightning Network
We can basically identify four main privacy guarantees that we want to achieve on Lightning Network:
-
Private channels and public channels
On Lightning Network you can create public channels and private channels.
To simplify, if Alice and Bob open a public channel, then it is announced to the rest of the network and all nodes can use it to route payments.
If, however, they decide not to disclose the details of this channel, it is classified as a private channel and no one else should be able to use it to route payments unless they know of its existence.
Some studies claim that about 30% of the total channels on the Lightning Network are private channels.
Therefore, the first guarantee of privacy we want on LN is that, if there is a private channel between Alice and Bob and Bob wants that private channel to be secret, it will remain secret and not be communicated to anyone.
This is unfortunately based on trust since Bob must trust Alice not to communicate this channel to the rest of the network and vice versa.
-
Secrecy of channel balances
The second privacy guarantee we want is the secrecy of channel balances. We do not want it to be known to third parties.
In the Lightning network, the capacity of each payment channel is in the public domain, it is something we cannot hide. If there is a payment channel between Alice and Bob, then its capacity is known to everyone.
The capacity of the channel is basically the sum of the individual balances of Alice and Bob, i.e. the two parts corresponding to the channel, and this information, even more detailed, is also known to Alice and Bob.
Specifically, Alice and Bob not only know the total capacity of the channel but also know the real-time status of the channel, i.e. how many satoshi are on Alice’s side and how many on Bob’s side. Alice and Bob know the individual balances in the channel, and we want this information to remain secret between them and hidden from other third parties.
-
Path-related anonymity
The third privacy property we want on the Lightning Network is route-related anonymity.
Suppose that Alice sends a payment to Bob and that this payment is routed through many intermediate nodes (and channels) such as Carol, David and Eddy. What we want is that, if we choose a random intermediary (e.g. David), then he should not be able to determine who is the sender and receiver of a specific payment.
Lightning uses the technique of onion routing: each node that routes a payment only knows the previous and next nodes to which the transaction should be routed.
Theoretically, if there is only one routing, we cannot defend ourselves because then it is already obvious who is the sender and who is the receiver; but also the length of the payment route is unknown to the intermediaries. Therefore, even if the payment only makes one intermediate step, the node between the parties is not able to determine whether the payment has one or two or three steps, etc. This is what is known as “route-related anonymity”.
-
Privacy of off-path payments
The fourth property we want on the Lightning Network is the privacy of off-path payments.
For example, let’s pretend that we are observers who want to spy on some users.
We pretend to have many channels with several nodes in the network; according to LN principles, we should not be able to tell what is happening along the channels that do not involve us as intermediaries of a payment.
If Alice sends a payment to Bob and there are intermediaries in between such as Carol and David, we should not be able to tell how many satoshi have passed along those payment paths, or even the existence that one or more transactions have occurred along those channels.
Conclusion
To conclude, Lightning Network does help users’ privacy in that, once a channel is opened, no further transactions are written on Bitcoin’s blockchain which, as we recall, is perennial, transparent and immutable.
However, one has to consider the current limitations of the Lightning Network, its pros and cons. LN is currently still in the study phase and many privacy issues still exist and need further development to be resolved, but the basis for operating with greater privacy exists and can help users protect their (crypto) financial information.
Everything stems from study and knowledge.
The post Lightning Network and Privacy: Is it really that private? appeared first on The Cryptonomist.






















