Bitcoin’s public and immutable nature necessitates the return of mixnets to achieve true network-level privacy.
Bitcoin was initially thought by many to be anonymous digital cash due to the fact that all transactions are conducted as peer-to-peer transfers between wallet addresses which serve as pseudonyms. However, the public nature of Bitcoin’s ledger of transactions (the “blockchain”) means anyone can observe the flow of coins. This means that pseudonymous addresses do not provide any meaningful level of anonymity, since anyone can harvest the counterparty addresses of any given transaction and reconstruct the chain of transactions.
This lack of privacy in Bitcoin has led to an important stream of work to make Bitcoin’s blockchain ledger itself private: ranging from centralized tumblers that mix coins in order to obscure their origin for a small service fee and extra delay; to sidechains with Confidential Transactions (as deployed by Blockstream’s Liquid) that hide the amount of a transaction on-chain using homomorphic encryption; to non-custodial mixing softwares like CoinJoin, in which a large group of users cooperates to combine multiple Bitcoin payments into a single transaction, to obfuscate the information of which spender paid to whom.
One simple solution is to get rid of self-surveillance of transactions by getting rid of the blockchain as much as possible. So another solution are the Layer 2 protocols, like the Lightning Network, a payment channel network where users can make, arbitrarily, many off-chain payments between themselves without the need to broadcast these individual transactions to blocks included in the Bitcoin blockchain.
However, the Achilles’ heel of Bitcoin privacy is actually its peer-to-peer broadcast. In detail, Bitcoin is built on top of a peer-to-peer broadcast at the level of TCP/IP packets, where both new transactions and blocks are announced to the rest of the Bitcoin network, making Bitcoin resilient against censorship. Yet, being resilient against censorship does not make one resistant against surveillance. Your IP (Internet Protocol) address leaks your approximate geolocation with every packet.
When a Bitcoin transaction is broadcast by a full node, an attacker can link transactions to the IP addresses of the originating user, as well as the timing and size of the transactions of the user. Anyone can do this by simply running a full supernode that connects to all of the thousands of Bitcoin nodes as well and simply observing the network traffic. Randomized delays in the P2P traffic as implemented by Bitcoin help a bit, but ultimately are capable of being defeated.
Similarly, an IP footprint is left at crypto exchanges and bitcoin payment providers. In fact, this kind of “traffic analysis” can even be applied to the Lightning Network. Not only can government agencies like the NSA commit these kinds of attacks, but even a local Internet Service Provider (ISP) can do traffic analysis on your connection to the internet from your home.
Without the network-level privacy of the peer-to-peer broadcast, any privacy solution for Bitcoin is like building a castle on top of sand, using fancy cryptography on the blockchain itself — including through so-called “privacy coins” like Zcash, and even Monero — when the fundamental peer-to-peer broadcast of Bitcoin is exposed for the whole world to see.
What can be done to provide privacy for your peer-to-peer broadcast on Bitcoin?
Bitcoin Over A VPN
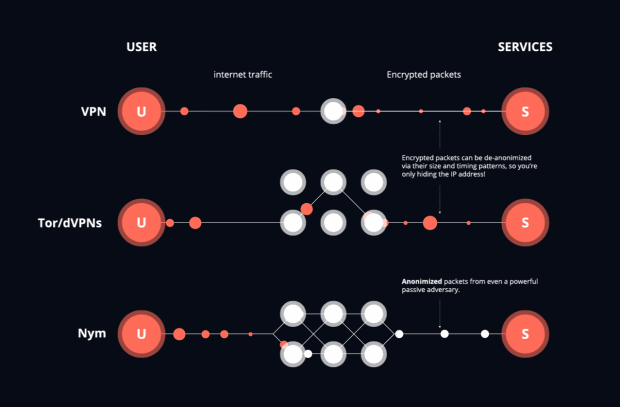
One solution to obfuscate the IP address is to use a VPN (“Virtual Private Network,” but better thought of as an encrypted internet proxy). In a nutshell, VPN software builds an encrypted tunnel between a client device and a server run by a VPN provider, which acts as a proxy that forwards the network communications. Thus, your local IP address doesn’t get linked to your wallet address or your identity on a KYC-supporting crypto exchange.
Yet, we’ve pointed out that VPNs are not actually anonymous. Although VPNs can hide your IP address, they suffer from inherent weaknesses due to their centralized trust model. A VPN provider acts as a trusted proxy and hence can easily link all of your activities at the network layer. The VPN itself also doesn’t need to monitor you, as anyone watching a VPN carefully can also link your transactions. Such network eavesdroppers can observe the network traffic flowing to and from the VPN proxy and simply track the routed network traffic based on the size and timing of the data packets, and thus easily infer your IP address even when the VPN is hiding your IP address from the website or Bitcoin full node you are accessing.
Most people don’t run a full Bitcoin node. Many people use exchanges, and even hardcore Bitcoin users who tend to use self-custodial wallets run light clients, where a full node acts like a trusted proxy like a VPN. However, don’t be fooled into thinking this full node provides privacy. The full node, and anyone watching the full node, can correlate your Bitcoin broadcasts and your transactions with your light wallet… and thus your IP address and transactions to you!
Bitcoin Over Tor
In contrast to centralized VPNs, Tor builds a decentralized network of nodes so that no single node knows both the sender and receiver of any network packet. Tor forwards traffic via a long-lived multi-hop circuit as follows: Each connected user opens a long-lived circuit, comprising three successive, randomly-selected relays: entry guard, middle relay and exit relay, and negotiates symmetric keys which are then used to encrypt each of the communication packets. While the message travels along the circuit, each relay strips off its layer of encryption, giving Tor its name as “The Onion Router.” If a Bitcoin transaction was sent over Tor, it appears to have the IP address of the last Tor exit relay.
Although much better than any VPN, Tor was designed to defeat local adversaries that observe only small parts of the network. Since packets still come out of Tor in the same order they came in, a more powerful adversary that can watch the entire network can use machine-learning to successfully correlate the pattern of internet traffic so the sender and receiver of a transaction can be discovered. This kind of attack can easily be applied to Bitcoin transactions over Tor, and recently, there has been evidence that large amounts of exit nodes have been compromised by a single entity. In fact, early Bitcoin developers preferred a pure peer-to-peer broadcast over using Tor for precisely this reason. Circuits in Tor also last ten minutes, so if more than one Bitcoin transaction is sent via Tor in this period, these transactions will all have the same IP address of the last Tor exit relay. New circuits can be built with every transaction, but this behavior stands out from Tor’s default and so is easily identified using machine learning.
Techniques like Dandelion that are used by Bitcoin resemble Tor, with each new packet being sent a multiple number of hops before being broadcast, where the hops are a “stem” and the broadcast are the “flower,” and so resembling a dandelion. Although it is much better to use Dandelion than to not use it, a powerful adversary can simply observe the building of the randomized Dandelion circuit and use that to de-anonymize the sender and receiver.
Bitcoin Over A Mixnet
Unlike Tor and VPNs, a mixnet mixes packets. This means that, rather than packets coming out of a node in the mixnet in the same order the packets came in, packets are delayed and then mixed with other packets, so the packets leave the mixnet in a different order.
As pioneered by David Chaum in his pre-Tor paper that invented mixnets in 1981, one way to think about them is that at each “hop” in the mix network, the mix node “shuffles” the packets like a deck of cards. Like Tor, a form of “onion encryption” is used and the packets are all made the same size using the Sphinx packet format. This is the same Sphinx packet that is used in the Lightning Network, but was originally built for mixnets.
Nym is a kind of mixnet where the packets are delayed using a statistical process that both allows an estimate of the average delay of a packet but provides maximum anonymity as it is unknown when any given packet is finished mixing. Packets are sent from a program like a Bitcoin wallet through a gateway, then three mix nodes, and finally out of a gateway. Unlike Tor and VPNs, the packets are each sent routed through the network individually. With Nym, dummy packets are added to increase the anonymity of packets.
Compared to Tor and VPNs, mixnets are well-suited for Bitcoin. Bitcoin packets naturally fit within Sphinx packets, as we’ve seen with the Lightning Network, and it makes more sense to route Bitcoin packets individually rather than through a circuit needed for a webpage.
Like VPNs and Tor, mixnets hide the IP address of the packet, but unlike Tor and VPN, each packet can be given a new route and exit IP address. Due to packets being sent out of order and fake packets being added, it is likely harder for machine learning to identify the sender and receiver of a packet. Bitcoin connections from wallets to full nodes would benefit from using a mixnet, as the broadcast would be much more thoroughly defended against attackers than just using Dandelion.
Although the re-ordering of packets naturally tends to make mixnets like Nym slower than Tor, the delay can still achieve reasonable anonymity — as long as enough people are using the mixnet! — within seconds to minutes. One way to view mixnets is as a slower, but more anonymous version of the Lightning Network.
Lastly, mixnets are not only for Bitcoin. Just as Tor is suitable for web browsing using synchronous circuits, mixnets are suitable for any kind of traffic that naturally fits into asynchronous messages such as instant messaging. One killer use-case of mixnets before Bitcoin was email remailers that forwarded email anonymously.
Early cypherpunks like Adam Back tried to bring mixnets to market to allow anonymous email in the Freedom Network. Back invented “proof of work” via Hashcash in part to prevent anonymous email spam, where even a small amount of work like solving a hash puzzle would prevent a malicious spammer from flooding people with anonymous email.
Cypherpunks ended up using mixnets like Mixmaster, co-created by Len Sassman, and Mixminion, co-created by George Danezis and the founders of Tor (before they started working on Tor), in order to hide their identities online. So, it should come as no surprise that concepts like proof of work that originated with attempts to create anonymous email with mixnets ended up in Bitcoin. It would not be surprising at all if Satoshi Nakamoto used a mixnet to hide their own identity on email discussion lists when releasing Bitcoin.
Right now, Tor and Dandelion are the best solutions we have for network-level privacy for Bitcoin, yet the return of mixnets will be necessary in order to allow Bitcoin to achieve true privacy and security against powerful — even nation-state level — adversaries.
This is a guest post by Harry Halpin And Ania Piotrowska. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.