Key Takeaways
- The dependence on centralized infrastructure creates single points of failure and degrades the promise of decentralization.
- Pocket Network addresses Web3’s access handling side with a censorship-resistant node network, zero downtime and no sunk cost to applications.
- Pocket is designed to facilitate a multichain future, integrating with over 40 blockchains and growing rapidly in average daily relay servicing (52x YoY) and the number of service nodes (24x YoY).
- Despite Pocket’s high inflation, the linear rewarding with serviced relay volume resulted in a 30% increase in total POKT supply in three months. Subsequent concerns around stakeholder dilution drove the DAO to tame inflation.
- Pocket’s upcoming massive V1 upgrade is a significant step towards a highly scalable network equipped with enterprise-grade service quality.
The recent Web3 proliferation has been quite a lure for the intellectually agile. Both builders and skeptics gathered around its fire and started participating in the show. With the recent market volatility, the stars guiding investors dimmed their lights on builders. Once perceived as rockstars, builders slowly gave the spotlight to skeptics, as if it was their time to shine. As large as the scope of commentary was, most of the balanced criticisms converged on specific argument patterns, with the incomplete decentralization of blockchain networks taking the lead.
On Tradeoffs
Critics often describe the networks as being built around an illusion of decentralization. They point out that hash rates have been consolidated into only a few mining pools and that smart contract platforms depend too much on private infrastructure providers, which could become centralized points of failure. Although these criticisms on the incomplete trustlessness problem are intrinsically valid, things tend to get more nuanced on the battlefield. When applications optimize for cost efficiency, they often opt for a centralization trade-off, especially when the costs significantly outweigh the benefits of decentralization. On top of that, centralized infrastructures provide high-quality service, making them a superior choice on multiple fronts.
As a means to an end, decentralization is potentially not a scalable design choice. To move away from a centralized infrastructure would require distributed solutions with enterprise-grade service qualities. Quality, cost, and decentralization are the three heads of the chimera that Web3 infrastructure providers need to execute in order to have a chance of broad adoption.
Pocket: Information Routing in a Blockchain Transaction
Enter Pocket Network, a full-node coordination engine. Pocket strives to become a leading decentralized access solution by simultaneously tackling three fronts: censorship-resistant RPC handling services, zero downtime, and no sunk costs.
The Pocket Network aims to disrupt a specific step in a regular blockchain transaction. For instance, in an Ethereum transaction, smart contracts are filled with logical, Ethereum Virtual Machine (EVM)-compatible directives. Whenever interacting with these contracts, users first need to submit their request to an Ethereum full node equipped with EVM. This full node can be a local or external node. If the user runs a local full node, they can read the chain data as well as validate the transaction to broadcast to the network without an external connector. However, running a full node is a costly and inefficient activity and is limited by performance issues such as downtimes and high latency. Instead of taking on this operational overhead, applications refer to node services to acquire chain data and handle their transactions.
Source: BlockChannel
Accessing a server, or in this case accessing a blockchain through an external node, requires the user to determine a first interaction point. Who will give the information about the chain state? Who will take the first transaction request in case of a write request? Which node will play the role of a customs and see if the submitted transaction is valid before releasing it to the chain? This first non-local interaction point is determined using RPC, an API that allows the application to send their request to a specified full node via a URL.
Every interaction, both state-changing transactions and information requests, involves this path. When users do a particular action on their wallet, it triggers a call, resulting in an API request routed to a full node. For example, Metamask chooses Infura as their default RPC endpoint provider. If a user wanted to send funds to another address or to check their own wallet’s token balance, Metamask would route their request to the nodes operated by Infura.
The lack of a well-developed decentralized alternative before Pocket Network made applications heavily rely upon centralized node providers such as Infura and Alchemy. The centralization of these gateways makes the network susceptible to single points of failure with unexpected downtimes and the threat of censorship. A fresh case of censorship occurred with Infura and Metamask accidentally blocking transactions originating from Venezuela.
Pocket Network’s decentralized RPC protocol is designed to obviate these kinds of problems with a distributed full-node network that is designed to be highly redundant. Contrary to the centralized incumbents who are bound to operational bottlenecks when expanding, Pocket Network is relieved of the burden of running their own nodes, operating similarly to prominent marketplaces like Uber and Airbnb. As a coordination-providing intermediary network, Pocket can remain chain agnostic, function as an L0 despite being an L1, and rapidly scale the services into new chains. So far, the network has been able to attract 34,000 service nodes (and counting) while expanding to more than 40 networks within a brief amount of time. Thus, Pocket became one of the fastest-growing decentralized infrastructure providers in the space.
How Pocket Helps Bridge Multiple Blockchain Worlds
Fundamentally, the design of the Pocket Network V0 is akin to the mythological tree Yggdrasil, with numerous network integrations reaching to blockchain worlds like branches, fostering them with essential information. Meanwhile, the service is grounded in three components like Yggdrasil’s three roots: application, nodes, and network layer.
In the Pocket ecosystem, applications are the agents operating on smart contract protocols like Ethereum and Harmony. They seek API request handling services from Pocket’s distributed node system, constituting the demand side of the network. On the market’s supply side dwell two types of nodes ensuring that the information bridging demand of applications is met: service nodes and validator nodes.
Anyone who downloads the chain history can run a full node and connect applications with relay handlers as well as being able to secure the network. However, Pocket requires nodes to stake at least 15,000 POKT to be eligible for handling application API requests and thus perform interchain information dissemination. These relay handlers are the service nodes that sit between the Pocket Network and the external blockchain, performing the essential part of the network’s magic by running a Pocket full node and at least one RelayChain node (a full node on integrated networks) to connect the applications with the external networks. Among these service nodes, the top 1000 by staked amount can become the validator nodes. Validators check if service nodes handle relays and forging blocks with valid transactions through the Pocket’s implementation of Tendermint PoS.
The third component, the network layer, is a set of rules that lies underneath, orchestrating critical operations such as application to service node coordination, reward and punishment mechanisms, and dispute settlements.
Real-world transaction
Although applications are the primary users of the Pocket Network, regular Web3 wanderers may also experience how the possible TCP/IP of the Web3 node infrastructure works by changing the Metamask RPC route to Pocket’s public nodes. Applications refer to Pocket’s facilitating website Portal to demand an RPC endpoint, which is currently the sole access point for applications. More direct and censorship-resistant integration through PocketJS will be enabled with permissionless app staking.
In contrast to the subscription-based payment model of the centralized providers, Pocket Network doesn’t request direct payment from applications to mint a dedicated RPC endpoint. Instead, it adopts a stake-to-use model that requires users to stake POKT in order to access services.
Applications can choose between a free tier or stake-based subscription. Pocket’s free tier option serves the same number of relays as Infura’s $225/mo subscription plan: 1 million relays/day. Applications can subscribe to the free tier, or preferentially, they can stake POKT and benefit from additional relaying services proportional to their staked amount (~130 relay/POKT at the time of writing). Nevertheless, app staking will not become permissionless until the protocol’s major V1 upgrade to ensure sustainable scaling and high-quality service. As it will remain capped to an arbitrary number of app stakes (currently 2,298) with the Portal able to share a stake between multiple applications, most applications subscribe to the free tier and let Pocket Foundation cover their entry costs.
Pocket’s access dashboard Portal is equipped with tools to support service quality. Before matching applications with service nodes, it runs a sync check and its Cherry Picker to make sure the nodes are synced to the chain’s current state and operate on low latency. As applications start using their dedicated URL to send information to a non-native chain (e.g., requesting to see the total deposit amount in an Aave lending pool), a Pocket full node dispatches their relaying request to the network and initiates a session between them and the service nodes.
Sessions are regularly updated data structures that dictate which service nodes handle relay requests of the application for a predetermined time interval. Currently, an application is matched with 24 service nodes in a session, and the relaying service continues for four Pocket blocks before getting tumbled. The same 24 nodes typically serve an application for approximately one hour before a new session starts and the application is paired with a new set of nodes.
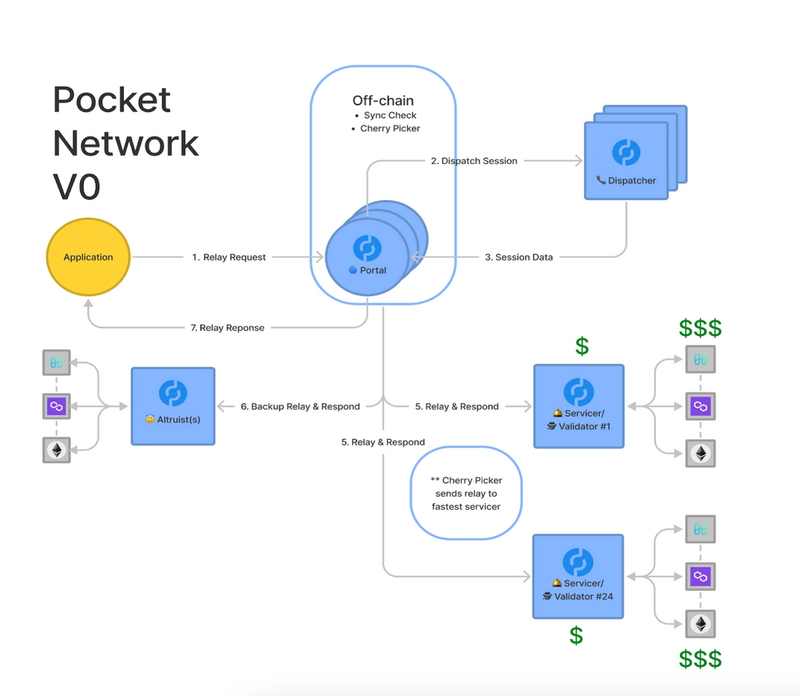
Source: Pocket Network
Service nodes route relay requests to and from the non-native chain and keep track of the number of relays delivered. After the session is complete, they bundle them in batches and send them as proof-of-relays to Finality Storage. Validator nodes check the legitimacy of proofs to see if service nodes indeed provided the service. Then they forge Pocket blocks with valid transactions.
At the end of the block production, if the relays are valid and the application didn’t invoke Challenge Transaction to challenge the proof-of-relay, the network mints tokens proportional to the volume of relays (currently 0.00843 POKT/relay). The reward pool is distributed among facilitators as such:
- Service Nodes: 89% of the minted POKT
- Pocket DAO: 10%
- Validator Nodes: 1%
Service nodes take the lion’s share of the rewards. Coupling this form of generalized mining that leverages POKT as a unit of work with the lucrative return potential for the service nodes, the network experienced quite the success in building the supply side. This translated into a ~24 times the YoY growth, currently sitting at over 34,500.
Add to this zero downtime, no sunk cost, and censorship-resistant service provision, as well as Pocket’s appealing free tier option. All of these have helped the network nurture the demand side of the market. Right now, the protocol handles over 200 million relays a day on average, indicating an increase of ~52x YoY. The significant uptick in average daily relays followed Pocket Network’s integration with Harmony in October 2021. As Harmony users had issues with the default RPC providers and switching to Pocket alleviate these problems, Pocket captured a substantial amount of the network traffic right after the integration. As of today, approximately 150 million of the >200 million daily relays originate from the Harmony network.
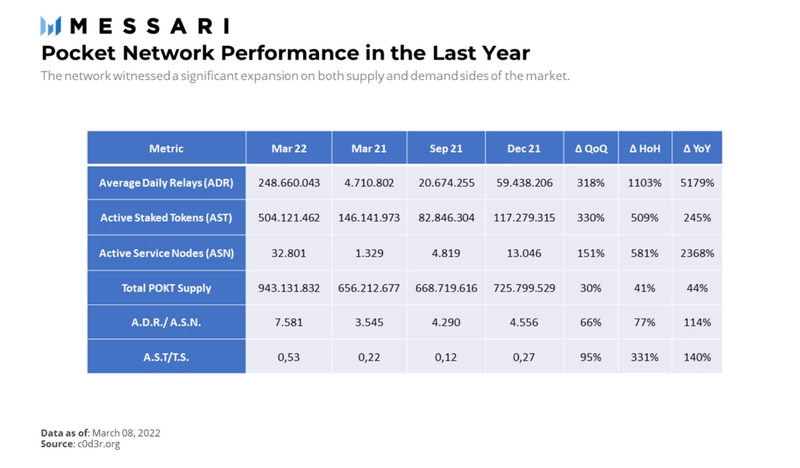
In 2021, the network served 6.4 billion relays to Harmony, followed by Ethereum with 3.7 billion. Although these numbers seem somewhat small compared to Infura’s 12 billion daily calls in 2019 and 2 billion daily eth_calls in 2020, the growth of the Pocket Network still merits attention. It took ten months for Pocket to hit the first billion cumulative relays milestone and only another six months to handle the same number of relays in less than a week.
Tokeneconomics and Reward Mechanism
There is a delicate relationship between a chain’s technical capabilities and its economic model. Both need to uniquely coincide to permit the desired coordination game to unfold with success. With community concern centered around the sustainability of highly inflationary tokeneconomics, the protocol’s economic life cycle is divided into three phases with which the POKT incentivization mechanism is calibrated to attain fast growth first and later switch to a more sustainable economy.
After establishing a solid supply side in the Bootstrapping Phase, the protocol is currently in its Growth Phase, where the high inflation rates are intrinsic to its expansion strategy. In the same way Pool 2 attracts liquidity in DeFi, the Growth Phase of the tokeneconomics model revolves around the economic flywheel where a high APR on the native token attracts service liquidity, which in turn accelerates the growth of relay service capabilities and network integrations.
When the growth of inflation becomes higher than the growth of total staked POKT supply and when the POKT price appreciates to a sustainable level, the Pocket DAO will initiate the
Maturity Phase
Overall, the POKT tokeneconomics is designed to attract long-term participants and diminish unproductive speculation. This vision is materialized in two instances: covertly banishing non-participant tokenholders from the network through high inflation rates and separating the right to governance from token holdership via merit-based vote claim.
However, the truth is there is growing inflationary pressure on staked tokens with increased network adoption, due to node providers getting paid with freshly minted tokens for their relaying services. The rapid increase in total token supply tarnishes Pocket’s low-cost stake-to-use payment model with a non-negligible dilution cost. Due to the protocol-implemented cap on staked apps, the discrepancy between the increased actual demand and total supply causes speculative price appreciation to remain essential for taming the turbulent difference sustaining the network growth.
To give a concrete example, the total POKT supply increased from 660 million to 960 million in the last six months, considerably diluting any application stake at the time. Yet, the inflation has been proportional to the increase in the number of relays. Hence, an increase in average daily relays combined with a speculative appreciation has offset the dilutive effect with an increase in overall network value, turning any upfront cost done at the time to a ~2x accounting profit.
In other words, the market demand allowed a positive ROI for the early adopters. However, after witnessing exponential growth in the last couple of months, the discrepancy between demand and supply became more apparent. The community acted quickly and recently passed two proposals to implement a more sustainable inflation mechanism. By adopting a gradually declining inflation, they aim to stabilize network dynamics and introduce protection to network stakeholders before any token burning starts.
As the inflationary pressures of Pocket’s linear token minting punish non-participant tokenholders during rapid network expansions, POKT speculators have sought ways to generate income with their tokens. The most popular solution has been node financing, where POKT holders allocate their tokens to node runners for a share of the service. This service can only be accessed through custodial services. Moreover, the amount of staked POKT has no influence over the selection chances for a session, causing service node operators to strategically distribute their POKTs to multiple wallets and maximize the number of eligible wallets they hold.
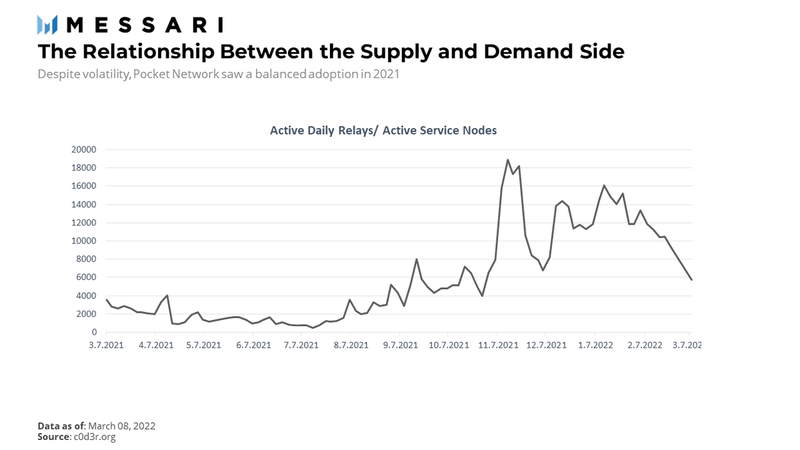
Both of these phenomenons have a magnifying effect on the supply, thus affecting assessments on the meaningful supply-side growth. Although Pocket’s ADR / ASN growth indicates that the network experienced a somewhat balanced adoption last year, a large portion of the relay handling capacity remains underutilized. Recently, the growth of the supply side started to significantly outpace the demand side, meaning that the average node profitability has been declining since its local peak on January 7, 2022.
V1 Upgrade
Until recently, one deal-breaker for apps was the high latency of the network compared to centralized solutions. However, Pocket managed to tackle this problem and achieve a competitive latency by increasing the number of nodes in a session from 5 to 24 and improving its latency filters.

Source: Internal test conducted by the Pocket Network team.
On top of that, the Pocket team is laser-focused on improving service quality with their massive V1 upgrade. The transition to V1 will comprise consequential alterations that will prepare the Pocket Network to scale its relay services by orders of magnitude. It aims to further lower the latency and boost the network in many ways with a novel chain architecture. Not expected to launch until at least the following year, the upgrade will offer new design mechanisms on four different modules of the chain: utility, consensus, peer-to-peer, and persistence.
Because Pocket Network must maintain a service quality on par with centralized competitors, they intend to incorporate massive enhancements to their incentivization and inspection mechanisms to further optimize the network for high-quality servicing.
A major change is the addition of a new network agent. The underutilization of proof-of-relay challenging (Client-side Challenge Feature) and the inconvenience attached to the fail-first-correct-later approach drove Pocket to introduce a new agent in V1, fisherman. Disguised as an application, this new agent will play the role of an inspector and score nodes on availability, latency, and consistency of their services.
Pocket’s V1 will also incorporate a quality-focused reward mechanism. In V0, Cherry Picker ranked nodes by their latency and made sure those with high latency got fewer chances for servicing. Like Cherry Picker’s filtering, this new mechanism will distribute relay rewards not according to the individual relay volume but to the test scores provided by fishermen.
Because scaling to handle trillions of relays requires a vastly robust infrastructure, Pocket’s V1 will focus on ensuring the network is ready to scale on all fronts. At the moment, Tendermint BFT requires extensive communication between nodes which causes a bottleneck for scaling the number of nodes. In V1, the protocol will adopt its own implementation of HotStuff BFT. This will be assisted with the introduction of task-specialized communication and an effective message dispersion method**.** Transitioning from random gossip of Tendermint BFT to structured gossip is expected to result in lower bandwidth usage and higher network efficiency.
The introduction of the quality-inspecting fishermen will also help network scale. Using these new agents, the network will be able to tinker with the protocol design to accommodate more clear-cut roles for nodes. Recently, the protocol separated tasks between validator nodes and service nodes to make sure they were less bound by each other’s requirements. V1 aims to double down on the specialization feature by stripping the responsibility of keeping track of relay proofs away from service nodes thanks to fishermen. Thus, the network will make requests handling the sole responsibility of service nodes and allow them to allocate resources to increase network efficiency.
V0 allowed developers to access RPC handling services with zero downtime and without the sunk cost of a subscription-based payment model. V1 will primarily focus on doubling down on the current value propositions instead of expanding the scope of operations. Since the permissionless app staking and the ultimate design for scalability won’t be unleashed until V1, the network’s true potential will remain unrevealed until this significant upgrade.
Conclusion
One may argue that the current permissioned state of Pocket’s Portal is a sign of faux decentralization. One could further their argument by saying that not all nodes are created equal according to Pocket’s proof-of-useful-work (generalized mining) mechanism. And the current node concentration might increase even more with professional node providers gaining an edge with V1 quality measures.
Firstly, it might be counter-productive to get lost in often mismatched linguistic interfaces while arguing about the definitions and immediately condemning a practice if it doesn’t exactly fit our ideal. Instead, it might be more pragmatic to take any endeavor that strives for diminishing the total censorable points of failure and consider it a cherishable improvement.
Secondly, Pocket aims to thwart these with the eventual transition to permissionless application access, optimizing efficiency in V1 to lower technical requirements to run a node, and introducing a more granular geolocalization to give small nodes a competitive edge. Therefore, its full decentralization is also subject to a gradual process.
Finally, Web3 needs a more decentralized infrastructure. As such, a multichain future dependent on seamless integrations between multiple networks requires decentralized infrastructure even more. As the focus for the last years primarily rested on enhancing the smart contract ecosystem with L2s and alternative L1s, the importance of decentralized middleware remains to be explored. With its distributed node network to tackle one of the pain points of the space, Pocket might be the missing point in the grand picture of decentralization as it carries the potential to help the space move away from centralized incumbents.
Critics might call the current permissioned state of Pocket’s Portal an example of faux decentralization. They might label Pocket’s proof-of-useful-work mechanism (generalized mining) an unfair advantage for professional node providers. But instead of arguing about semantics, the focus of the conversation should be on Pocket’s endeavor to diminish the total censorable points of failure, which is a cherishable improvement. Beyond that, Pocket aims to refute its critics’ claims by gradually transitioning to permissionless application access, optimizing efficiency in V1 to lower the technical requirements to run a node, and introducing a more granular geolocalization to give small nodes a competitive edge.
Pocket’s eventual move to full decentralization will meet Web3’s need for a more decentralized infrastructure. Because a multichain future depends on the seamless integration between multiple networks, the focus for the last several years has been on enhancing the smart contract ecosystem with L2s and alternative L1s. With its distributed node network acting as a decentralized middleware, Pocket Network can become the key to helping the space move away from centralized incumbents.
This report was commissioned by Pocket Network, a member of Protocol Services. All content was produced independently by the author(s) and does not necessarily reflect the opinions of Messari, Inc. or the organization that requested the report. Paid membership in the Hub does not influence editorial decision or content. Author(s) may hold cryptocurrencies named in this report and each author is subject to Messari’s Code of Conduct and Insider Trading Policy. Additionally, employees are required to disclose their holdings, which is updated monthly and published here. Crypto projects can commission independent research through Messari Protocol Services. For more details or to join the program, contact hub@messari.io. This report is meant for informational purposes only. It is not meant to serve as investment advice. You should conduct your own research, and consult an independent financial, tax, or legal advisor before making any investment decisions. Past performance of any asset is not indicative of future results. Please see our terms of use for more information.



















