How companies react to growing cyber-attacks and the criticality of the individual in the web3.
The Digital Transformation has reinvigorated the economy of many companies that have transformed and enhanced their business by embracing the digital world and the web, a real injection of technology to improve products, production processes, communications, increasing productivity and ease of use.
However, there has been no shortage of problems linked to this transformation which, on the flipside of the coin, have increased the cyber-crime attack surface, exposing companies to ever greater risks that are not always entirely predictable due to the very nature of technology, which overwhelms anyone who is not prepared, or rather, up-to-date.
Systematic inconsistencies according to Moody’s report
A survey conducted by Moody’s, a private rating agency based in New York, which is responsible for producing economic and financial research, has shown that the growing threat of cyber risks has prompted many companies to intensify investment in this area in an attempt to increase their defences to cope with the continuing escalation of attacks, yet there are still many gaps in the preparation of companies and organizations in the management and prevention of attacks.
Despite the increased focus, defensive capabilities are not keeping pace with the industry’s increased investment in cybersecurity and the increasing variability of attacks, demonstrating that qualified personnel are far from easy to recruit and find, while threats are becoming more sophisticated and attackers more prepared.
The report was conducted by surveying more than 5,000 financial companies, government agencies and utilities with 60 questions between 2020 and 2021 and assessed three main categories of cyber resilience: cyber risk governance, operational risk management and cyber risk transfer.
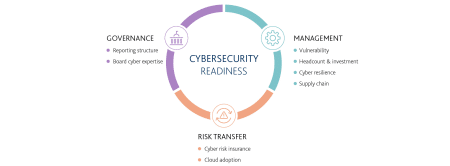
The paper found that there are a number of inconsistencies in this area, many of the cybersecurity officer positions vary widely across sectors, for example, and the companies they work for rarely disclose attacks they have suffered to the public, showing a discrepancy between the reports that boards of directors receive from security officers on time, and their disclosure to the public.
The IT Governance analysis indicated how much attention was paid to security issues, strategies, roles and tools used by companies. It showed that where this knowledge is more solid at the top of the company, such as on the board of directors, there is more attention and more operationality at lower levels rather than the other way around.
Even in the presence of highly trained cyber managers, it shows that only a small percentage of cyber managers report directly to the CEO or CFO, generally the two highest-ranking officials within an organization. At this juncture, the most virtuous companies were those related to financial services, with more detailed and timely reports, revealing more than double the attention to these aspects, considering them very relevant compared to the public sector, which showed the most evident gaps in cyber security.
The biggest gap, according to the report, is the lack of a standard for notification and assessment of attacks adopted at global level: this makes it more difficult to identify the severity of threats and therefore their resolution and management, and also affects public disclosure, which is important not only for transparency, but especially for the predictability of risks that could be shared between companies, thus anticipating future attacks.
On 9 March 2022, the Securities and Exchange Commission (SEC) issued an amendment to its cyber-attack reporting guidelines, which are specifically designed to better inform and prepare investors for risk management and security governance strategies that require early intervention and notification of incidents.
Since there are no legal requirements for reporting guidelines, companies are less likely to disclose them, and instead try to keep attacks secret to protect their customers and investors. In sectors where these guidelines are enforced by law, there is a better alignment between cyber preparedness and cyber investment.
Another gap highlighted in the report is between the use of basic and advanced security strategies, with companies lagging far behind in these areas and struggling to keep up with the times. The distribution of investments is unusual, with a large part of the funds going into insurance to cover the damage caused by attacks, rather than investing in training and prevention.
Basic IT security skills are also increasingly in demand among company employees, who are often considered the weakest link in an exposure to cyber-attacks. The percentage of employees trained has risen by double digits since 2018 in almost all sectors, with the exception of the public sector, which is once again at the bottom of the list. In the most careful companies, there has been a whirlwind turnover to achieve the desired standards and results.
Investment in cybersecurity is growing rapidly as the picture shows: annual growth in IT investment was 15% in 2019 and 17% in 2020.
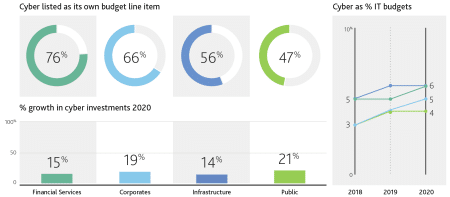
Not only has investment in the procurement of tools and skilled personnel increased, but so has investment in maintaining these standards, which require ongoing maintenance and upgrades. However, there remains a considerable proportion of companies that do not yet have cyber security as a specific line item.
According to the findings of the analysis, the most common countermeasures can be found by adopting prevention rather than resolution systems, and many of these strategies are constantly put into practice by keeping the focus high at all levels and roles:
- Vulnerability scans, designed to detect known weaknesses that can be exploited in the company’s network, computers and applications by the attacker.
- Incident response plans generally consist of documented plans that outline the procedures to be followed in the event of a security breach, the specific people required in the response and their specific roles. These plans are most effective when regularly tested, reviewed and updated.
- Multi-factor authentication. Widely adopted in most sectors, particularly by financial institutions (95%) and corporations (90%), it is one of the best defences when coupled with qualified personnel at all levels within the company.
- Weekly data backups to a system disconnected from an organizsation’s network are an effective way to quickly restore operations after a ransomware attack. These attacks typically encrypt a victim’s files, hindering or disrupting operations until the attacker provides a ransom key (ransomware) or the victim successfully restores their systems using existing backups.
- Cyber risk assessments aim to capture data to identify cyber vulnerabilities before making a takeover and integrate new defensive tools.
But the general attention, given the ever-increasing number of threats and their complexity combined with the ease of sophistication of security measures has led companies to arrange different tests and increase the training of qualified personnel; here are the most common ones:
- Penetration testing (pen test) is the simulation of a cyber attack to assess an organization’s Internet-accessible applications and networks.
- Tabletop excercises, actual exercises used to test an organization’s incident response plans, including tools, procedures and competence in responding to different cyber attack scenarios.
- Red Team Testing, is a more focused form of penetration testing that typically involves an internal and external team using real-life attack tactics to test an organization’s physical and cyber security defences and incident response plans.
Long-term unsustainability
As we have seen, companies and organizations are pouring their attention and funds into cyber security, but this is generating some serious discrepancies. The lack of qualified personnel, the choice of pouring funds on insurance instead of preventive actions, the growing gap between the private and public sectors, have meant that many attacks in recent years have caused enormous damage, according to the most recent estimates around 13 million dollars per company globally, with an increase of 12% in the last year.
Insufficient countermeasures account for 45% of these numbers, and as the frequency of attacks increases, from an average of 45s to as much as 11s, this leads to a scenario with greater risk exposure and higher costs for companies.
Web3 and the crypto world
While web2 has shown how important it is for companies to keep up to date and increase their cyber-security budgets, with web3 the focus will have to shift to the individual who, as the nerve centre of their information, will have to invest in training to safeguard their data.
More and more cyber threats are linked to web3 tools and services, of which the crypto world is full, and where the most effective attacks are still those of social engineering, a sign of the profound unpreparedness of the end user.
The various cryptocurrency exchanges are adapting more than any other sector, paying a great deal of attention both internally by adopting all the strategies and tools necessary to deal with threats, but above all trying to train the end-user with documentation, papers and also with learn-to-earn programmes designed to reward the end-user by fulfilling important tasks on security and knowledge of the tools that the platform offers, recognizing the weak link in their own system in those who use it.
“Technical problems can be remediated. A dishonest corporate culture is much harder to fix”. – Bruce Schneier
The post Global cyber security in companies and the web3 appeared first on The Cryptonomist.