Key Insights
- Current decentralized application (dapp) governance is investor-centric and gives no power to users, especially when protocols store state.
- Usage-based governance primitives could allow tokens to fulfill fundraising concerns and transparent changes to protocol parameters while protecting users.
- Sybil resistance is essential to good governance, and the research and building in Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs) is positioned to be one of the biggest growth areas in crypto.
Introduction
“Good news…you came a long way. Bad news…you went the wrong way.” – J. Cole on Token Governance.
Crypto, an industry born on game theory and incentive alignment, has failed to implement these principles in decentralized application governance, so far.
Usage-based governance with Sybil resistance can create a more equal playing field for both investors in and users of a protocol. Users are not represented in the governance of most decentralized applications (dapps). Instead, they are often at the mercy of the largest tokenholders.
Current State
Layer-1 protocols such as Bitcoin, Ethereum, and ZCash employ “New York City” governance, where users or validators who do not agree with protocol changes can “go fork yourself!” This governance mechanism forces alignment between users and validators because of the reliance on each other: you cannot have one without the other. It also allows for plurality: any group can fork a chain, retain historical state, and apply its own parameters.
Although most dapps are open-sourced and allow anyone to fork code, you cannot fork the state of a dapp. For example, you can create Lido2 with zero fees, but you cannot move the ETH in Lido’s smart contracts to your own.
To adjust parameters, most dapps use token-based governance. But the inability of users to fork the state of the protocol leaves them at the mercy of tokenholders’ whims. This empowers monopolies to extract value from users.
The Argument For Monopolies
A strong counterargument is that monopolies rise because a network adds value to users. Therefore, at maturity, the network should be able to extract value.
To build a network is not cheap, whether it is ridesharing, an electric grid, or a liquidity marketplace for providers to receive fees from traders. So the value proposition to investors and builders should be convincing. If they build it, shouldn’t they reap some benefit from it?
Many cry for public goods, which is ideal, but in a self-sovereign world, it is only rational to expect individuals to optimize their time and resources for their own gain.
Crypto Can Do Better
Usage-based governance is a way to protect users from monopolies.
This opens a vast design space for builders. Usage-based governance should define a lookback period to determine vote weights, as well as decaying or enhancing weights, based on the length of a user’s history.
Usage-based governance creates a new playing field where investors have to work within the confines of direct user protection. For example, parameter changes can enter an optimistic contract that will execute changes tokenholders vote on, unless users veto the changes. If users do not allow holders to pass any changes that benefit them, users will lose out on the best builders. There is again a necessary alignment between the two.
Potential Implementations
Protocols can create a usage ledger that updates a wallet’s usage statistics each time the wallet interacts with the protocol. The governance contract can then give voting rights to users based on the stored state in the usage contract. This on-chain storage would increase gas costs for transacting on the protocol and also increase gas for governance/voting.
DAOs could also use off-chain ledgers to reduce the gas cost, in exchange for verifiability risk. A new governance interface could be developed alongside Snapshot where DAOs can define the metrics that determine vote-weighting. Wallets verify ownership, and the off-chain ledger defines their voting power. The methodology would have to be open-sourced and then measuring voting power for users could be tracked with simple queries.
Other solutions could leverage oracles, subgraphs, or a new governance primitive or standard.
Sybil Resistance
What is The Sybil Problem?
Obviously, just ask the Open AI ChatGPT bot:
The Sybil problem is a problem in computer science and game theory in which a single entity is able to create multiple identities or pseudonyms in a network in order to manipulate the outcome of decisions made within that network. This can lead to a situation in which the entity with multiple identities is able to unfairly influence the decision-making process to its own advantage. The Sybil problem is particularly relevant in the context of peer-to-peer networks, where multiple entities can communicate and interact with each other without the need for a central authority.
Sybil Resistance, then, is the battle to determine if each entity has a unique owner or not. Kevin Owocki, founder of Gitcoin and host of the Green Pill podcast, calls it “sock puppet resistance.” A game in which attackers try various methods to control entities that would otherwise seem sovereign and defenders must make the game expensive or be able to identify bad actors and entities.
Why Fight the Fight?
Effective Sybil resistance enables a one-human-one-vote governance system. It makes the system more democratic, enabling equity based on humanity rather than resources.
In the case of usage-based governance, as opposed to token-based governance, it is likely even more important to have Sybil resistance. If the goal of the implementation is to protect users, there exists a risk that a large player could Sybil attack the usage-based governance process to earn votes and undermine the goal of protecting users. Manipulating usage statistics is much cheaper than buying tokens, especially on low-cost chains or rollups.
A heralded solution to balance meritocracy while increasing democracy is quadratic voting (QV). Unfortunately, almost no existing governance mechanisms utilize quadratic voting. There are three explanations for this:
- There has not been a good way to enforce Sybil resistance or collusion.
- Often it is the creators of and investors in the protocols who would lose control if QV were implemented. Airdrops are a good example: there are conflicting incentives for protocol teams who want to increase usage of their protocol. Enabling Sybil attacks is likely good for usage to bootstrap the protocol.
- QV can be seen as less meritocratic, as a power-user or large investor would have a diluted voice relative to their usage/investment.
Gitcoin is one of the only protocols reliant on effective Sybil resistance. Gitcoin helps fund grants using quadratic funding to determine how much of the matching pool should be awarded to grantees (rewarding the projects that attract the largest number of supporters rather than the most dollars supported).
Current Arsenal
A difficulty with Sybil resistance is akin to the Heisenberg problem: if you detect the Sybils, they will change their behavior. Kevin Owocki likes to describe it as an ongoing battle between the red team (attackers) and the blue team (defenders). Therefore, a reactive defense to Sybil attacks that detects/identifies them ex-post will always be a cat-and-mouse game.
The two leading defense strategies in the Sybil resistance game use two different deterrence strategies: increasing the cost of a Sybil attack or establishing unique identities.
The foremost example of the first strategy is Bitcoin’s Proof-of-Work network. To control multiple miners, you must expend significant resources. Upala, an anti-Sybil system for dapps, creates a market for the price of forgery of a wallet.
Other solutions enable verifiable credentials (VCs) to signal uniqueness of digital identifiers (DIDs) for wallets.
Digital identity, itself, is a tricky bag. The Declaration of Independence of Cyberspace clearly makes the need for privacy. Different DIDs can be ranked on a privacy-preserving to Sybil security axis, though it is more of an art than a science. Some builders, like Evin McMullen of Disco, are working on consent for off-chain verifiable credentials, which would give a middle ground of users consenting to remove privacy for certain VCs at certain times or to certain parties.
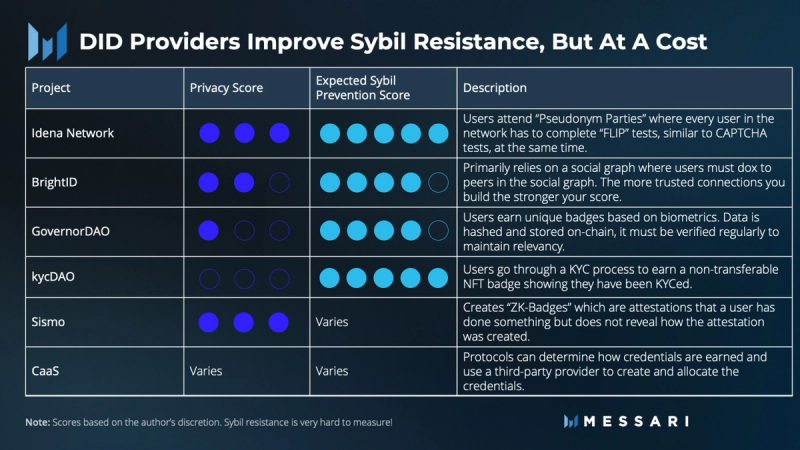
Gitcoin recently released the Gitcoin Passport. It is a new primitive, built on Ceramic (itself a key primitive for DIDs), for builders to implement Sybil resistance in their protocols. The protocol can determine which “stamps” it values or requires. “Stamps” are distinct digital identity verifiers. Protocols can also specify a scoring mechanism for these stamps to determine a trust score for an account based on the DIDs it has.
The Frontier
The nature of crypto is very conscious of privacy preservation. Therefore, many are researching zero-knowledge (ZK) technology that will hopefully enable users to store data on-chain while also controlling access to that information.
Teams are also building social graphs such as Lens Protocol and Farcaster. A social graph gives DIDs reputational value. Building is just beginning, but social graphs could possibly be used for unique user verification in the future.
There is no shortage of use cases for DIDs. Joe Lubin and ConsenSys have been long backers of entrepreneurs in the space, and founders of Gitcoin, Disco, SpruceID, and others spun out of Consensys. Since then, many new projects have sprouted and benefitted from recent improvements in ZK tech. This could be one of the hottest areas of the bear market.

Source: Towards Digital Self-Sovereignty: The Web3 Identity Stack, by Nichanan Kesonpat
Many of the other projects and ideas mentioned above are still at an early stage. A key difficulty will be growing the network. Many of them, especially the social-graph-based solutions, get stronger the larger they get. Some projects, like Worldcoin and Martin Koppelmann’s Circles, embed universal basic income to attract users. However, a stronger appeal will likely be needed. Perhaps adding Sybil-resistant usage-based governance will empower many to strengthen their unique DIDs.
Conclusion
Governance in crypto is a novel implementation of decentralization. Current forms are problematic on many axes, but one of the largest problems is the lack of user-tokenholder alignment. Relying on tokens to be both a fundraising tool and an alignment tool may not be the best solution. Usage-based governance can help, creating an economic game where users and economic interests must be symbiotic. Sybil resistance is important for usage-based governance. There are growing solutions to the Sybil resistance problem, but the key to success for all of them is to make an extraordinary use case.
Recommended reading / listening not linked earlier:
Green Pill Podcast, Kevin Owocki
Who Watches the Watchmen? A Review of Subjective Approaches for Sybil-resistance in Proof of Personhood Protocols , Paula Berman et al.
Towards Digital Self-Sovereignty: The Web3 Identity Stack, Nichanan Kesonpat
Soulbond, Vitalik Buterin et al.
Moving Beyond Coin Voting Governance, Vitalik Buterin