Key Insights
- Founded in 2019, CESS is a decentralized data value infrastructure supporting applications across sectors such as DePIN, AI, and DeSci. It emphasizes enhanced data privacy, sovereignty, and security through decentralized storage and delivery solutions.
- CESS introduces key technologies – including DeOSS (Decentralized Object Storage Service), Random Rotational Selection (R²S), Proof of Data Reduplication and Recovery (PoDR²), Proof of Idle Space (PoIS), Proxy Re-encryption Technology (PReT), and Multi-Format Data Rights Confirmation (MDRC) – to enhance decentralized data management, storage security, privacy preservation, and collaborative AI capabilities.
- CESS introduces a system architecture incorporating a Blockchain Layer, Distributed Storage Resource Layer, and Content Decentralized Delivery Network (CD²N) to manage decentralized data storage and content distribution.
- The Decentralized Object Storage Service (DeOSS) provides secure and scalable storage, integrating encryption and load balancing for robust data management.
- XESS AI Protocol Suite, through CESS AI-LINK, facilitates decentralized collaborative AI model training without exposing underlying datasets, preserving data privacy and sovereignty.
Introduction
As the Web3 ecosystem evolves, the need for secure and decentralized data value infrastructure becomes increasingly important. Traditional centralized systems, while efficient and scalable, often struggle with data privacy breaches, security risks, and single points of failure. As data volumes grow, these systems face increasing challenges in maintaining security, privacy, and user control. The concentration of data within a small number of centralized entities can expose sensitive information to unauthorized access, creating systemic risks.
Enter CESS, a decentralized data infrastructure created with the goal of addressing these vulnerabilities. CESS leverages a distributed node network, encryption, and a blockchain-based disaster recovery system to enhance data privacy, integrity, and resilience. A key feature of CESS is its focus on securing frequently accessed “hot” storage within a decentralized framework, mitigating vulnerabilities inherent to high-access data in distributed environments.
Unlike conventional cloud storage providers relying on centralized data centers, CESS redistributes data across independent storage nodes. This architecture promotes availability, censorship resistance, and resilience while enabling data monetization and allowing users to maintain full ownership rights. CESS encourages individuals and organizations to retain control of their digital assets, providing mechanisms for permissioned access without compromising security.
Furthermore, CESS’s architecture integrates with critical sectors such as Decentralized Physical Infrastructure Networks (DePIN), Artificial Intelligence (AI), and Decentralized Science (DeSci). This integration fosters cross-sector innovation and collaboration, with security and privacy in mind. The platform’s approach is particularly significant in industries where data transparency, provenance, and security are critical, offering a distinct solution for decentralized data value infrastructure that addresses the evolving needs of the Web3 ecosystem.
Website / X (Twitter) / Discord / Telegram
Background
CESS, founded in 2019, is a data value infrastructure designed to support the growth of decentralized applications across various sectors, including DePIN, AI, and DeSci, enhancing data privacy, sovereignty, and security through decentralized storage and delivery solutions. CESS engages in policy discussions and industry standardization efforts with entities such as the Blockchain Association, Government Blockchain Association (GBA), and the Institute of Electrical and Electronics Engineers (IEEE). On Dec. 27, 2023, CESS announced a Series A fundraising of $8 million, with investments from DWF Labs, Infinity Ventures Crypto, Web3 Foundation, 7 O’Clock Capital, and HTX Ventures, among others.
The core leadership team of CESS consists of:
- Nicholas Zaldastani (Co-Founder, Chairman, and Marketing Lead of CESS) has experience in technology, venture capital, and scaling companies. From 1988 to 1994, Zaldastani served as Director of Oracle, leading international marketing and product management. With a degree from Harvard Business School and a background in business strategy and growth, he brings leadership experience to the development of CESS’s decentralized data value infrastructure.
- Joseph Li (Co-Founder and Chief Technology Officer of CESS) specializes in decentralized cloud storage and Web3 data security. With network security and blockchain architecture expertise, Li plays a key role in developing CESS’s scalable, secure data-sharing solutions. He has earned certifications from the Blockchain Council, reinforcing his technical background in decentralized systems.
- Jessie Dai (Co-Founder and Chief Operating Officer of CESS) is a trader, entrepreneur, and early crypto investor. Dai serves as Vice Chair of the Web3 Standardization Association (Hong Kong), where she contributes to the development and adoption of Web3 technologies. With a background in blockchain strategy and ecosystem growth, she plays a role in CESS’s operations, partnerships, and industry engagement, driving the adoption of decentralized data infrastructure.
Technology and Architecture
CESS aims to serve as a foundational data value infrastructure for data-driven applications, decentralized AI models, and next-generation Web3 ecosystems. Its data value infrastructure is designed to integrate with Decentralized Physical Infrastructure Networks (DePIN), artificial intelligence (AI), and Decentralized Science (DeSci), ensuring that data remains sovereign and accessible for use across various industries.
Key Technology
CESS introduces a variety of technologies to reinforce its data value infrastructure:
Random Rotational Selection (R²S) Consensus Mechanism
CESS implements a proprietary consensus protocol called Random Rotational Selection (R²S). R²S selects 11 consensus nodes within each six-hour era based on a composite scoring system, promoting unbiased and decentralized node participation.
The scoring methodology integrates three distinct components:
- Reputation Score: Reflects historical performance metrics such as uptime, reliability, and overall contributions to the network.
- Staking Score: Represents the cumulative total of a node’s staked CESS tokens and any tokens delegated by nominators.
- Random Score: Derived from a Verifiable Random Function (VRF), this component introduces unpredictability into the node selection process, reducing potential manipulation.
Node scores reset at the beginning of each era, offering all eligible nodes equal opportunities for validator selection. Nodes selected as validators produce blocks and receive token-based incentives, whereas nodes demonstrating poor performance or malicious behavior face penalties that negatively impact future selection probability.
Proof of Idle Space (PoIS) and Proof of Data Reduplication and Recovery (PoDR²)
To verify storage reliability and safeguard data integrity, CESS details two proof mechanisms:
- Proof of Idle Space (PoIS): Verifies that storage miners are providing the storage capacity they have committed to. It uses randomly generated, verifiable placeholder data to measure each miner’s available storage accurately. This ensures miners cannot falsify storage capacity, confirming that validated idle space is reliably available for user data storage.
- Proof of Data Reduplication and Recovery (PoDR²): Allows stored user data to be secure, recoverable, and consistently available. It leverages fault-tolerant erasure coding combined with Proof of Data Possession (PDP) methods, periodically challenging storage nodes to provide cryptographic proofs of data integrity. PoDR² also handles the recovery and redistribution of data segments if storage nodes fail or leave the network.
Proxy Re-encryption Technology (PReT)
CESS integrates Proxy Re-encryption Technology to facilitate encrypted data sharing and distribution. Through PReT, data owners can grant selective access to their encrypted data segments to authorized entities without revealing sensitive information. This approach prioritizes data confidentiality, limits visibility exclusively to authorized recipients, and prevents unauthorized data exposure or access.
CESS AI Agent Hub
The CESS AI Agent Hub serves as a coordination point for autonomous AI agents, enabling interactions across various industry applications. This hub promotes interoperability, allowing agents from diverse systems and organizations to collaborate.
CESS AI-LINK
At the core of CESS’s AI integration lies the CESS AI-LINK, which enables collaborative training of AI models without requiring participants to expose or share their original datasets. Leveraging smart contracts, AI-LINK securely distributes computational tasks among decentralized GPU resources provided by participating network nodes. This mechanism maintains the confidentiality of user data, preserving data sovereignty.
Multi-format Data Rights Confirmation (MDRC)
CESS employs the Multi-format Data Rights Confirmation (MDRC) mechanism to protect data rights and ensure content authenticity. MDRC assigns each data file a unique data certificate ID by extracting and recording its digital fingerprint. This mechanism utilizes fingerprinting algorithms tailored to several data types (e.g., text and image). MDRC facilitates the detection of data rights violations by comparing digital fingerprints across the network and supports content integrity by tracking data provenance.
DeOSS
CESS introduces DeOSS (Decentralized Object Storage Service), a decentralized object storage system that provides data storage capabilities within the Web3 ecosystem.
The architecture of DeOSS comprises two layers:
- Interface Layer: Acts as an entry point, offering standardized APIs and interfaces compatible with traditional object storage protocols (e.g., S3 compatibility). Users interact with DeOSS through API requests for uploading, retrieving, and managing stored content, requiring minimal parameters for access.
- Service Layer: Contains functional modules responsible for data processing, scheduling, peer-to-peer (P2P) communications, and interactions with the underlying blockchain. This layer manages data encryption, redundancy, segmentation, and distribution across storage nodes.
DeOSS integrates several features designed to support its decentralized infrastructure:
- Chunked and Resumable Upload/Download: Files uploaded to DeOSS are divided into smaller manageable chunks, allowing uploads and downloads to pause and resume.
- Encryption and Security: DeOSS employs multiple encryption schemes, including symmetric encryption (AES), asymmetric encryption, and proxy re-encryption, to secure data in transit and at rest. Proxy re-encryption facilitates secure data sharing by enabling controlled data access to authorized entities without exposing original encryption keys.
- Location-Based Storage Selection (LBSS): Allows users to specify storage nodes or regions for their data, preventing unauthorized geographic access.
- Censorship Resistance: DeOSS mitigates risks associated with censorship, unauthorized data blocking, or deletion.
- Scalability and Customization: DeOSS supports expansion and customization based on user needs. It allows load balancing, elastic resource scaling, and integration of additional functionalities tailored to specific use cases or applications.
- Data Distribution: DeOSS utilizes a caching network of globally distributed nodes, optimizing data retrieval performance and latency. It employs data scheduling strategies for content delivery, enabling users to access data independent of their geographic location.
Collectively, DeOSS provides an HTTP API-based decentralized object storage system compatible with standard object storage interfaces (such as Amazon S3 compatibility), supporting an array of file types, including images, audio, video, application backups, and Web3-native content.
System Architecture
CESS also introduces a modular, coupled architecture comprising three core components: the (i) CESS Protocol Suite, (ii) XESS AI Protocol Suite, and (iii) Interface.
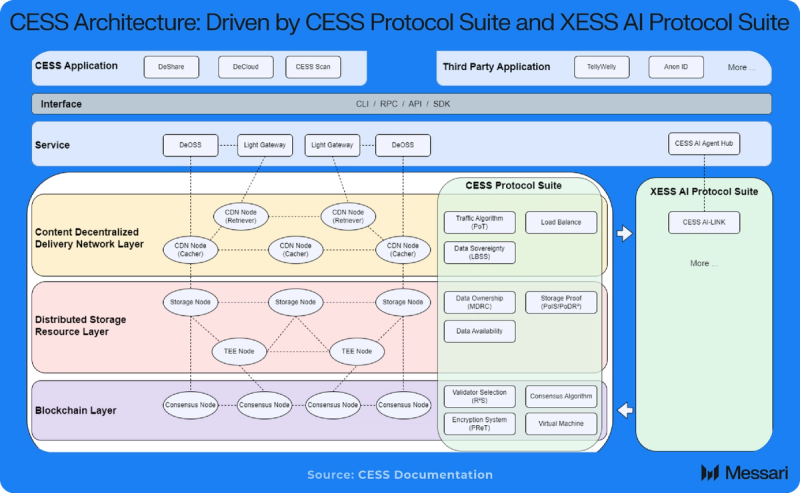
CESS Protocol Suite
The CESS Protocol Suite is foundational infrastructure for CESS and contains three layers:
- Blockchain Layer: Offers blockchain functionalities and incentivizes the contribution of idle storage and computational resources, enabling data storage and data rights verification.
- Distributed Storage Resource Layer: Utilizes virtualization technology to aggregate and manage storage resources, comprising Storage Nodes (for data storage and management) and Trusted Execution Environment (TEE) Nodes (for computation and data processing).
- Content Decentralized Delivery Network Layer (CD²N): This layer assigns caching mechanisms through specialized Cache and Retriever Nodes to distribute and access data content.
The Blockchain Layer
On its own native blockchain, CESS provides a full technology stack to facilitate its data value infrastructure, mainly focusing on securing frequently accessed “hot” storage.” This multi-layered stack serves as the foundation of CESS’s native blockchain.
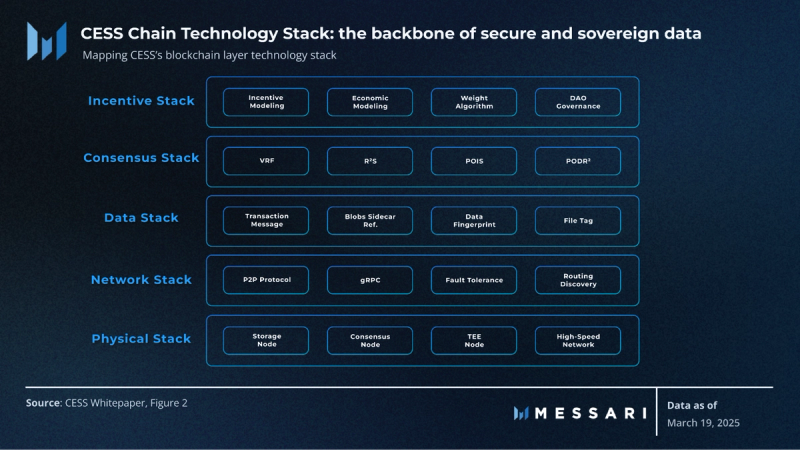
Each component of CESS’s blockchain layer technology stack is structured to fulfill a distinct role in the network:
- Incentive Stack: Establishes the incentive mechanisms regulating the ecosystem’s reward distribution. Key components include incentive models, economic modeling, weight algorithms, and DAO governance.
- Consensus Stack: Defines the protocols that govern network agreement on data validity and operations. It includes protocols such as VRF, R2S, PoIS, and PoDR2.
- Data Stack: Manages data storage, processing, and verification through transaction messaging, block sidecar references, data fingerprinting, and file tagging.
- Network Stack: Incorporates P2P protocols, fault tolerance mechanisms, and routing discovery to enable secure communication between nodes on the network.
- Physical Stack: Comprises storage nodes, consensus nodes, TEE nodes, and high-speed network infrastructure to form the foundational hardware layer of the CESS network.
Operating as a public blockchain is fundamental to CESS’s decentralized nature. It distributes data across a network of nodes rather than relying on a central server. CESS provides three types of global resources: computer, network, and storage. This technology stack enhances the system’s resilience against outages and attacks, a critical vulnerability of centralized systems.
In detail, the network’s robustness is further strengthened by its high-speed Content Decentralized Delivery Network (CD²N), which optimizes data delivery and retrieval. The CD²N enables data to be accessed regardless of the user’s location. This is achieved through a network of geographically distributed nodes that cache and serve content.
The Distributed Storage Resource Layer
The Distributed Storage Resource Layer is a core component of CESS, designed to aggregate and pool decentralized storage resources through virtualization techniques.
It primarily encompasses Storage Nodes and TEE Nodes/Workers.
- Storage Nodes form the core storage infrastructure, contributing unused bandwidth and storage capacities to the network. Data is securely stored by first being encrypted, replicated, and fragmented (sharded), ensuring redundancy, high security, and resilience against data breaches. Individual storage nodes retain only segments of complete data files, further safeguarding user information from unauthorized access.
- The TEE Nodes/Workers provide secure computational environments for verifying data integrity and generating data tags that prevent tampering. When Storage Nodes receive data fragments, they request and obtain data tags from TEE Workers, validating and protecting stored content.
Furthermore, the layer employs fault-tolerant erasure coding that users can configure according to data sensitivity, enabling data recovery even if multiple fragments become corrupted or lost. Storage nodes regularly undergo randomized integrity verification challenges triggered by consensus nodes and validated by TEE Nodes. This verification mechanism is designed to enhance data reliability and integrity within the network.
The Content Decentralized Delivery Network (CD²N)
CESS’s CD²N layer utilizes caching and P2P methodologies to optimize the speed and efficiency of data distribution. The network efficiently routes data directly into client-controlled domains, improving media accessibility while decreasing operational costs and minimizing the dependence on extensive proxy server networks. The network’s cache proxy servers address the seed limitations commonly encountered within traditional P2P frameworks by maintaining availability, provided that source nodes remain active.
The design of CD²N allows multiple storage nodes to store and serve identical content simultaneously. Users, in turn, can retrieve data from several nodes concurrently, enhancing download speed and reliability. Proxy nodes construct an autonomous P2P network, connecting storage nodes that do not possess publicly accessible IP addresses, thus retaining data sovereignty.
Key aspects of the CD²N include:
- Load Balancing: The CD²N layer applies adaptive load-balancing techniques to efficiently distribute network traffic across nodes, preventing bottlenecks and significantly improving network responsiveness.
- Edge Computing Integration: By incorporating edge computing technologies, the network processes data closer to end-users, decreasing latency and boosting content delivery speeds. Edge nodes also facilitate real-time processing and caching.
- Scalability: Designed to scale resources according to demand, CD²N can quickly deploy additional nodes during high-traffic periods and subsequently reduce resource usage during lower-demand phases.
- Security and Privacy: CD²N incorporates robust encryption and secure key management strategies to protect data during transmission and in idle. Integration with blockchain technology further provides immutable transaction records.
- Fault Tolerance: Built-in mechanisms proactively identify node failures, enabling rebalancement to operational nodes.
- Analytics and Monitoring: Equipped with comprehensive analytical tools, CD²N provides visibility into network performance, user interactions, and content utilization.
- Network Interoperability: The CD²N infrastructure facilitates integration with external CDN and P2P networks.
Governing the CD²N layer is the Decentralized Object Storage Service (DeOSS), functioning as an encryption intermediary, access control gateway, and content distribution platform within the CESS network.
XESS AI Protocol Suite
The XESS AI Protocol Suite leverages CESS’s existing data value infrastructure and privacy-preserving computational mechanisms to support decentralized AI applications. At its core, the XESS AI Protocol Suite standardizes essential AI functions such as distributed model training, inference processes, and AI-driven applications.
Central to the XESS AI Protocol Suite is CESS AI-LINK, a Byzantine fault-tolerant system specifically engineered to facilitate AI model training. Through CESS AI-LINK, participants collaborate in AI model training without sharing their underlying datasets. Smart contracts within the CESS network allocate computational tasks to various nodes, including single GPUs, GPU clusters, or decentralized GPU resources provided by Web3 DePINs. The suite interacts directly with the broader CESS architecture via an Interface Layer, ensuring interoperability between AI functionalities and the decentralized network components.
The Interface
Connecting the CESS Protocol Suite and the XESS AI Protocol Suite is the Interface, which facilitates interaction and communication between each of the protocol suites. The Interface bridges protocol interaction by defining a set of rules and conventions that enable each protocol’s various components to work together and operate CESS. By establishing a defined set of rules, CESS abstracts its internal implementation details, allowing external components to interact using predefined functions and parameters without requiring knowledge of the underlying implementation methods.
Closing Summary
CESS establishes a decentralized data value infrastructure built upon a multi-layered system architecture. Central to this is the proprietary Random Rotational Selection (R²S) consensus mechanism and storage verification methods, such as Proof of Idle Space (PoIS) and Proof of Data Reduplication and Recovery (PoDR²). Advanced technological modules, including Proxy Re-encryption, CESS AI-LINK, Multi-format Data Rights Confirmation (MDRC), and the DeOSS storage system, aim to enhance data sovereignty, secure sharing, and privacy-preserving capabilities. CESS’s architecture positions it as a potential solution for data value complications among DePIN, AI, and DeSci ecosystems.




















