Key Insights
- Humanity Protocol is an identity verification network that uses palm biometrics to verify user liveness and generate onchain credentials.
- Using the Proof-of-Humanity protocol, palm scans are converted into ZK-proofs that attest to human uniqueness without storing or sharing palm scans.
- Users can issue verified credentials, proving traits like age or residency through non-transferable Human IDs without relying on third parties.
- The Moongate acquisition brings onchain ticketing to Humanity. It issues non-transferable tickets to verified Human IDs to prevent scalping and enforce authenticity without ID checks.
Primer
Humanity Protocol (H) is a decentralized network built on Arbitrum that leverages palm biometrics to verify users’ liveness and identity. Founded by a team of experts in cryptography, distributed systems, and privacy tech, Humanity addresses the rising challenges of AI-driven fraud, Sybil attacks, and the rising demand for verifiable, self-custodied credentials.
Humanity’s Proof-of-Humanity protocol uses palm scanners or a mobile app to enroll and verify humans. After a user’s palm is scanned, the protocol generates a cryptographic proof that can’t be reverse-engineered or linked to the original image, ensuring no biometric data is stored and users retain control over their identity. Instead of storing biometric data, the system generates a hash tied to a Human ID, which can be verified using zero-knowledge (ZK) proofs, a cryptographic method by which users can prove they possess certain knowledge. This allows users to prove liveness, or even individual traits like age or residency, without revealing documents or biometric images. Users reverify using surface palm prints from the user’s mobile device or infrared vein scans from a palm scanner to confirm verified credentials.
The H token is the native asset of Humanity Protocol and will be used for validator incentives and governance. To ensure Sybil resistance from the outset, the initial token distribution was conducted through a “Fairdrop”, granting H to verified human users, including the community’s early contributors, Kaito stakers, Discord members, and ecosystem builders.
Website / X / Discord / Telegram
Building on Proof-of-Humanity with Identity Verification
Sybil attacks, in which a single entity creates and controls many fake identities, have long plagued digital ecosystems by undermining the fairness of governance and airdrops. If control over the network is achieved, Sybil attacks can even result in network censorship. The rise of AI has intensified this problem, since bots can now mimic human behavior, generate convincing synthetic identities, and bypass traditional defenses with increasing accuracy. As a result, verifying humanity online has become a complex challenge with broad implications for trust, fairness, and security.
Conventional solutions are increasingly inadequate. CAPTCHAs, the most rudimentary line of defense against bots, are now routinely bypassed with AI. More stringent “humanity checks”, including quizzes or behavioral analysis, often frustrate genuine users while failing to outsmart rapidly evolving bots. Meanwhile, identity checks that rely on uploading government IDs or personal information are not only intrusive and slow but also expose sensitive data to risks of misuse and breach.
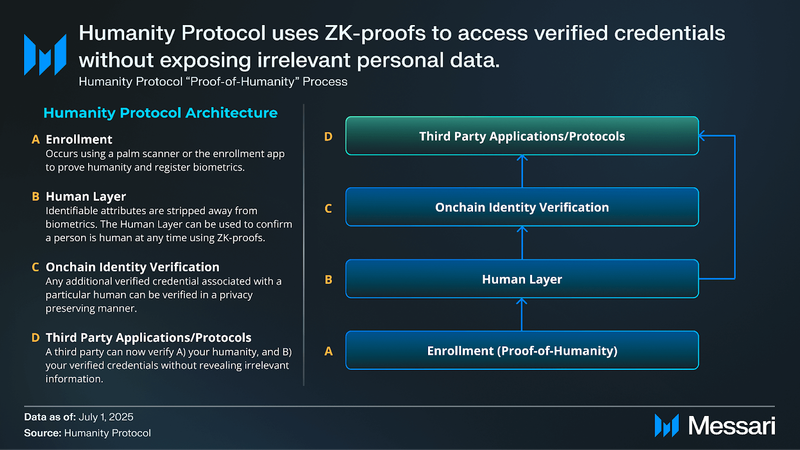
Proof-of-Humanity directly addresses these limitations. The protocol uses surface palm prints from the user’s mobile device or infrared vein scans from a palm scanner. The process involves scanning a user’s palm to generate a cryptographic representation that cannot be reverse-engineered or linked to the original biometric image. This privacy-preserving approach ensures that no raw biometric data or personal information is stored on centralized servers, so users retain complete control over their identity.
Humanity Protocol extends Proof-of-Humanity into an onchain identity verification system by allowing verified users to generate and present verified credentials (VCs). Without exposing underlying data, these cryptographic attestations linked to a Human ID confirm specific traits, such as age, residency, or event access. This is achieved via ZK-proofs. Users can demonstrate possession of a credential, such as being over 18, without disclosing their birthdate. The proof itself is sufficient for verification and is processed directly onchain. Credentials are non-transferable and bound to a single Human ID, which prevents delegation or resale.
The total addressable market for privacy-preserving identity spans both Web2 and Web3 and is being addressed by major companies like Microsoft, Apple, and Google. Onchain use cases include voting, airdrops, and compliance-constrained applications such as KYC (Know Your Customer) in DeFi. In Web2, fintech, education, and gaming sectors often require repeated KYC processes or third-party credential validation that could expose users to unnecessary risk. Existing solutions are concentrated among centralized providers and data brokers. A decentralized system that supports programmable, user-owned verification offers a structural alternative with broad application.
Proof-of-Humanity Use Cases
AI Deepfake Detection
AI-generated personas are increasingly difficult to distinguish from real users. Deepfakes can now mimic voice, facial patterns, and typing behavior with high fidelity, eroding trust online. Existing verification tools, such as CAPTCHAs or behavioral filters, fail to detect synthetic actors at scale and often degrade user experience.
Humanity Protocol addresses this by tying digital identity to biometric verification at enrollment. Each user is cryptographically proven to be a unique, live human. Unregistered humans would be required to present a palm (which a deepfake cannot achieve) and match that palm in the future to reverify their liveness.
Other Partnerships
Conventional KYC and identity verification systems rely on exchanging raw personal data, raising privacy, compliance, and security risks. Additionally, enterprises must collect and store identity records for regulatory purposes, which increases operational overhead and liability. The process is slow for users and exposes sensitive information to centralized systems with poor transparency. A more efficient, privacy-preserving approach has become vital as regulatory pressure increases and users seek greater control over their data.
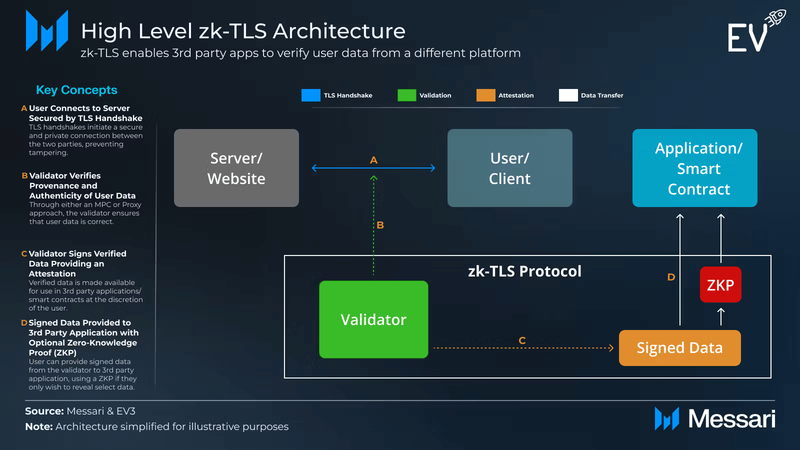
Humanity Protocol’s ZK-TLS framework replaces this model with cryptographic proof. Rather than uploading documents, users can prove specific identity traits, such as human verification or geographic eligibility, without disclosing underlying data. ZK-TLS captures a TLS handshake (allows two parties to authenticate each other over the internet, establishing a secure channel for transferring data) between a user and server, allowing a validator to verify attributes like age or residency without exposing raw data. The validator signs the verified data, which the user can convert into a zero-knowledge proof and submit to an application. This lets third parties confirm identity traits without accessing the underlying information.
ZK-TLS can be used in a range of identity-gated settings, including:
- Regional compliance: Verify location eligibility for token sales or financial products without revealing geographic data.
- Private logins: Authenticate users on education, gaming, or content platforms without storing credentials.
- Event access: Verify ticket ownership or attendance eligibility without exposing personal identity.
Humanity’s network design preserves privacy, reduces the need for data storage, and supports identity verification across both Web2 and Web3 environments without central trust dependencies.
Onchain Ticketing and the Moongate Acquisition
The ticketing market faces persistent issues with bot scalping, counterfeit sales, and resale manipulation. Existing systems often require identity disclosure to enforce authenticity, but do not guarantee that tickets are issued to or used by real people. As ticketing moves onchain, these problems are reappearing in new forms.
Humanity Protocol’s acquisition of Moongate brings biometric identity into onchain ticketing infrastructure. Tickets are issued directly to Human IDs cryptographically tied to a verified individual using a hash. Because these IDs are non-transferable and backed by zero-knowledge proofs, only real, unique users can claim or use a ticket. Organizers can validate attendance or grant post-event access without compromising privacy. This design removes the need for document-based checks, limits scalping at the protocol level, and enforces ticket authenticity without requiring document upload or ID scanning.
Closing Summary
Humanity Protocol treats identity as a cryptographic primitive rooted in biological uniqueness. Replacing document-based systems with real-time, proof-based verification introduces a model where users can confirm who they are or what they qualify for without exposing underlying data. This reduces attack risk, limits data exposure, and creates a composable identity layer suitable for any application that requires trust in human users.
The recent launch of the H token, distributed via a Sybil-resistant Fairdrop to verified human users, reflects the protocol’s identity-first design and commitment to decentralized participation from the outset. With tools like ZK-TLS, non-transferable Human IDs, and the acquisition of Moongate, Humanity Protocol is building infrastructure for applications that require verified, private identity across Web2 and Web3. As identity becomes increasingly rooted in digital systems, Humanity Protocol aims to address a global market spanning finance, governance, AI, and real-world access control.